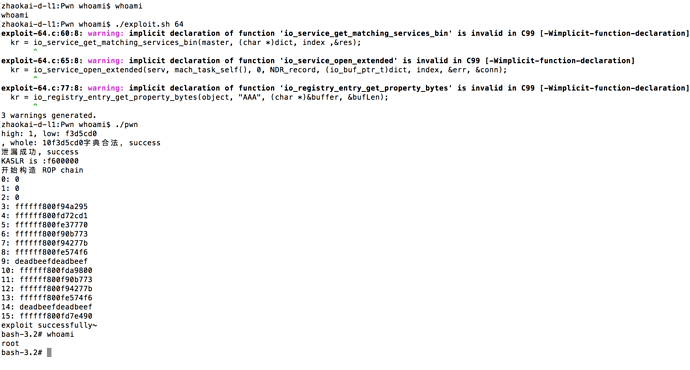
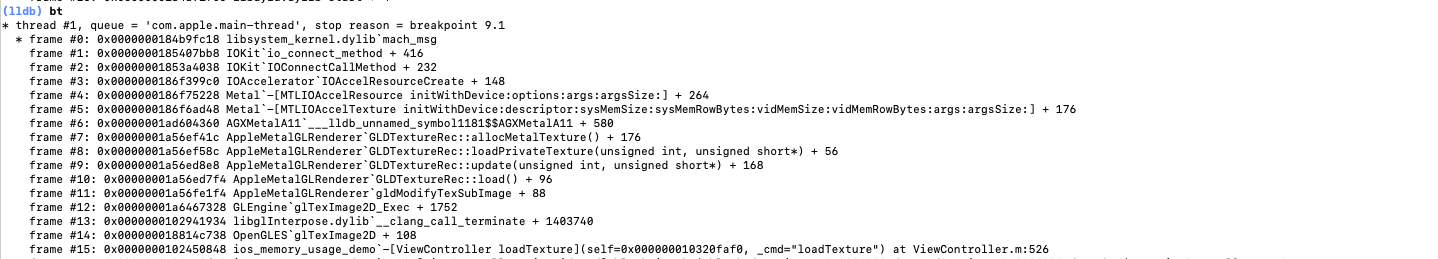
越狱设备使用 debugserver + lldb 进行动态调试的环境配置请参考狗神的文章:一步一步用debugserver + lldb代替gdb进行动态调试,这里就不再馈述。
本文只有两个目的:
- 说一下在iOS12系统下搭建调试环境时使用的一些不一样的操作。
- 提供一些iOS12系统下调试时遇到的问题的解决方法。
这里只针对iOS12(iOS11的设备已经压箱底了😂),是对自己折腾过程的一点总结,希望对坛友有一些帮助。
一、配置 debugserver
如果设备是使用unc0ver越狱的(还有其他越狱工具?),那么越狱工具的作者@Pwn20wnd已经把拷贝debugserver到设备的过程写成了一个脚本,路径为/usr/local/bin/debugserver。
ssh到设备中,输入debugserver其实就是调用这个脚本文件。这个脚本文件的内容可以看下,大概就是判断设备是否挂载了开发工具,如果挂载并且本地文件/usr/bin/debugserver不存在,那么就会执行签名+拷贝动作,将/Developer/usr/bin/debugserver使用/usr/share/entitlements/debugserver.xml文件签名,然后复制到/usr/bin/debugserver。有了这个脚本,可以省掉很多麻烦。
需要注意的是,/usr/share/entitlements/debugserver.xml的内容其实有点问题,需要调整,否则使用这个权限文件签名后的debugserver会有各种奇怪问题,文件原内容(随着越狱作者的更新,文件内容可能不一样):
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>com.apple.springboard.debugapplications</key>
<true/>
<key>com.apple.backboardd.launchapplications</key>
<true/>
<key>com.apple.backboardd.debugapplications</key>
<true/>
<key>com.apple.frontboard.launchapplications</key>
<true/>
<key>com.apple.frontboard.debugapplications</key>
<true/>
<key>run-unsigned-code</key>
<true/>
<key>seatbelt-profiles</key>
<array>
<string>debugserver</string>
</array>
<key>com.apple.diagnosticd.diagnostic</key>
<true/>
<key>com.apple.security.network.server</key>
<true/>
<key>com.apple.security.network.client</key>
<true/>
<key>com.apple.private.memorystatus</key>
<true/>
<key>com.apple.private.cs.debugger</key>
<true/>
</dict>
</plist>
需要修改成:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>com.apple.backboardd.debugapplications</key>
<true/>
<key>com.apple.backboardd.launchapplications</key>
<true/>
<key>com.apple.frontboard.debugapplications</key>
<true/>
<key>com.apple.frontboard.launchapplications</key>
<true/>
<key>com.apple.springboard.debugapplications</key>
<true/>
<key>com.apple.system-task-ports</key>
<true/>
<key>get-task-allow</key>
<true/>
<key>platform-application</key>
<true/>
<key>run-unsigned-code</key>
<true/>
<key>task_for_pid-allow</key>
<true/>
</dict>
</plist>
在iOS12上,任何命令行程序要想成功运行,不出现kill:9,除了使用ldid签名以外,还需要在权限文件中增加以下权限
<key>platform-application</key>
<true/>
修改后,手动删除/usr/bin/debugserver,然后重新执行debugserver即可安装好debugserver。
iPhone-7:~ root# rm /usr/bin/debugserver
iPhone-7:~ root# debugserver
二、解决各种奇怪问题
按照上面的流程配置好debugserver后,执行调试时,可能出现以下问题。
1. failed to attach to process named: “”
iPhone-7:~ root# debugserver localhost:1111 -a UCWEB
debugserver-@(#)PROGRAM:LLDB PROJECT:lldb-900.3.85
for arm64.
Attaching to process UCWEB...
error: failed to attach to process named: ""
Exiting.
错误信息说的很清楚了,就是找不到名字叫UCWEB的进程。尝试启动UCWEB后再执行命令即可。
2. Failed to get connection from a remote gdb process
iPhone-7:~ root# debugserver 127.0.0.1:1111 -a UCWEB
debugserver-@(#)PROGRAM:LLDB PROJECT:lldb-900.3.85
for arm64.
Attaching to process UCWEB...
Listening to port 1111 for a connection from localhost...
Failed to get connection from a remote gdb process.
Exiting.
解决方案:
- USB连接可能不稳定,重新插拔一下。
- 设备上可能已经有一个进程占用了端口
1111,导致无法连接(最常见的是有一个debugserver正在运行),这种情况下,直接ps -e看下是否有debugserver已经在运行,是的话就使用命令结束它killall -9 debugserver,或者直接尝试换一个调试端口。
- 可能是你签名
debugserver的权限文件中包含以下权限导致
<key>com.apple.security.network.server</key>
<true/>
<key>com.apple.security.network.client</key>
<true/>
<key>seatbelt-profiles</key>
<array>
<string>debugserver</string>
</array>
我不确定,不过权限文件最好是和我上面配置debugserver时的文件内容一致,至少我使用上面的权限签名后没有出现这个问题。
3. rejecting incoming connection from ::ffff:127.0.0.1
iPhone-7:~ root# debugserver *:1111 -a WeChat
debugserver-@(#)PROGRAM:LLDB PROJECT:lldb-900.3.57..2
for arm64.
Attaching to process WeChat...
Listening to port 1111 for a connection from *...
error: rejecting incoming connection from ::ffff:127.0.0.1 (expecting ::1)
这种情况偶尔会出现,不知道是什么原因,解决办法是指定使用ipv4地址
手机端:
iPhone-7:~ root# debugserver 127.0.0.1:1111 -a WeChat
电脑端:
(lldb) process connect connect://127.0.0.1:1111
4. Terminated due to code signing error
调试时,进程自动退出,并且提示签名错误。
(lldb) c
Process 9295 resuming
Process 9295 exited with status = 0 (0x00000000) Terminated due to code signing error
这个问题在iOS12上应该普遍存在吧?不知道为毛没人提问?难道只有我人品这么好?
这个是签名问题,可以使用大神@Morpheus______写的QiLin(麒麟)工具来绕过,他写了一篇文章来说明如何使用工具来解决这个问题,可以参考一下,文章针对的是iOS11的越狱设备。
我根据他的文章+ToolKit+思路,写了一个简单的可执行程序debugserverXII来帮助解决签名错误的问题,经过测试(iPhone7,iPhone9,1,iOS12.0),工作良好。
到目前为止,QiLin(麒麟)ToolKit默认只支持如下设备和系统,原文地址:
//iOS 12.1.2 - iPhone X
{ "12.1.1", "iPhone11,2", "D331AP", "_kernproc", 0xfffffff00913c638},
{ "12.1.2", "iPhone11,6", "D331AP", "_kernproc", 0xfffffff00913c638},
{ "12.1.1", "iPhone11,6", "D331AP", "_kernproc", 0xfffffff00913c638},
{ "12.1.1", "iPhone10,6", "D221AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.2", "iPhone10,6", "D221AP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.1.1 - iPhone X
{ "12.1.1", "iPhone10,6", "D221AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.1", "iPhone10,6", "D221AP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.1 - iPhone X
{ "12.1", "iPhone10,6", "D221AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.1", "iPhone10,6", "D221AP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.0.1 - iPhone X
{ "12.0.1", "iPhone10,6", "D221AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0.1", "iPhone10,6", "D221AP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.0 - iPhone X
{ "12.0", "iPhone10,6", "D221AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0", "iPhone10,6", "D221AP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.1.2 - iPhone 8 Plus
{ "12.1.2", "iPhone10,5", "D211AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.2", "iPhone10,5", "D211AP", "_kernproc", 0xfffffff0076660d8},
{ "12.1.2", "iPhone10,5", "D211AAP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.2", "iPhone10,5", "D211AAP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.1.1 - iPhone 8 Plus
{ "12.1.1", "iPhone10,5", "D211AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.1", "iPhone10,5", "D211AP", "_kernproc", 0xfffffff0076660d8},
{ "12.1.1", "iPhone10,5", "D211AAP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.1", "iPhone10,5", "D211AAP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.1 - iPhone 8 Plus
{ "12.1", "iPhone10,5", "D211AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.1", "iPhone10,5", "D211AP", "_kernproc", 0xfffffff00766a0d8},
{ "12.1", "iPhone10,5", "D211AAP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.1", "iPhone10,5", "D211AAP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.0.1 - iPhone 8 Plus
{ "12.0.1", "iPhone10,5", "D211AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0.1", "iPhone10,5", "D211AP", "_kernproc", 0xfffffff00766a0d8},
{ "12.0.1", "iPhone10,5", "D211AAP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0.1", "iPhone10,5", "D211AAP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.0 - iPhone 8 Plus
{ "12.0", "iPhone10,5", "D211AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0", "iPhone10,5", "D211AP", "_kernproc", 0xfffffff00766a0d8},
{ "12.0", "iPhone10,5", "D211AAP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0", "iPhone10,5", "D211AAP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.1.2 - iPhone 8
{ "12.1.2", "iPhone10,4", "D201AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.2", "iPhone10,4", "D201AP", "_kernproc", 0xfffffff0076660d8},
{ "12.1.2", "iPhone10,4", "D201AAP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.2", "iPhone10,4", "D201AAP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.1.1 - iPhone 8
{ "12.1.1", "iPhone10,4", "D201AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.1", "iPhone10,4", "D201AP", "_kernproc", 0xfffffff0076660d8},
{ "12.1.1", "iPhone10,4", "D201AAP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.1", "iPhone10,4", "D201AAP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.0.1 - iPhone 8
{ "12.0.1", "iPhone10,4", "D201AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0.1", "iPhone10,4", "D201AP", "_kernproc", 0xfffffff00766a0d8},
{ "12.0.1", "iPhone10,4", "D201AAP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0.1", "iPhone10,4", "D201AAP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.0 - iPhone 8
{ "12.0", "iPhone10,4", "D201AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0", "iPhone10,4", "D201AP", "_kernproc", 0xfffffff00766a0d8},
{ "12.0", "iPhone10,4", "D201AAP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0", "iPhone10,4", "D201AAP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.1.2 - iPhone X
{ "12.1.2", "iPhone10,3", "D22AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.2", "iPhone10,3", "D22AP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.1.1 - iPhone X
{ "12.1.1", "iPhone10,3", "D22AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.1", "iPhone10,3", "D22AP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.1 - iPhone X
{ "12.1", "iPhone10,3", "D22AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.1", "iPhone10,3", "D22AP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.0.1 - iPhone X
{ "12.0.1", "iPhone10,3", "D22AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0.1", "iPhone10,3", "D22AP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.0 - iPhone X
{ "12.0", "iPhone10,3", "D22AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0", "iPhone10,3", "D22AP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.1.2 - iPhone 8 Plus
{ "12.1.2", "iPhone10,2", "D21AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.2", "iPhone10,2", "D21AP", "_kernproc", 0xfffffff0076660d8},
{ "12.1.2", "iPhone10,2", "D21AAP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.2", "iPhone10,2", "D21AAP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.1.1 - iPhone 8 Plus
{ "12.1.1", "iPhone10,2", "D21AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.1", "iPhone10,2", "D21AP", "_kernproc", 0xfffffff0076660d8},
{ "12.1.1", "iPhone10,2", "D21AAP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.1", "iPhone10,2", "D21AAP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.1 - iPhone 8 Plus
{ "12.1", "iPhone10,2", "D21AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.1", "iPhone10,2", "D21AP", "_kernproc", 0xfffffff00766a0d8},
{ "12.1", "iPhone10,2", "D21AAP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.1", "iPhone10,2", "D21AAP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.0.1 - iPhone 8 Plus
{ "12.0.1", "iPhone10,2", "D21AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0.1", "iPhone10,2", "D21AP", "_kernproc", 0xfffffff00766a0d8},
{ "12.0.1", "iPhone10,2", "D21AAP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0.1", "iPhone10,2", "D21AAP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.0.1 - iPhone 8 Plus
{ "12.0", "iPhone10,2", "D21AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0", "iPhone10,2", "D21AP", "_kernproc", 0xfffffff00766a0d8},
{ "12.0", "iPhone10,2", "D21AAP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0", "iPhone10,2", "D21AAP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.1.2 - iPhone 8
{ "12.1.2", "iPhone10,1", "D20AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.2", "iPhone10,1", "D20AP", "_kernproc", 0xfffffff0076660d8},
{ "12.1.2", "iPhone10,1", "D20AAP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.2", "iPhone10,1", "D20AAP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.1.1 - iPhone 8
{ "12.1.1", "iPhone10,1", "D20AP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.1", "iPhone10,1", "D20AP", "_kernproc", 0xfffffff0076660d8},
{ "12.1.1", "iPhone10,1", "D20AAP", "_rootvnode", 0xfffffff0076660c0},
{ "12.1.1", "iPhone10,1", "D20AAP", "_kernproc", 0xfffffff0076660d8},
//iOS 12.1 - iPhone 8
{ "12.1", "iPhone10,1", "D20AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.1", "iPhone10,1", "D20AP", "_kernproc", 0xfffffff00766a0d8},
{ "12.1", "iPhone10,1", "D20AAP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.1", "iPhone10,1", "D20AAP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.0.1 - iPhone 8
{ "12.0.1", "iPhone10,1", "D20AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0.1", "iPhone10,1", "D20AP", "_kernproc", 0xfffffff00766a0d8},
{ "12.0.1", "iPhone10,1", "D20AAP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0.1", "iPhone10,1", "D20AAP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.0 - iPhone 8
{ "12.0", "iPhone10,1", "D20AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0", "iPhone10,1", "D20AP", "_kernproc", 0xfffffff00766a0d8},
{ "12.0", "iPhone10,1", "D20AAP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.0", "iPhone10,1", "D20AAP", "_kernproc", 0xfffffff00766a0d8},
//iOS 12.1.2 - iPhone 7 Plus
{ "12.1.2", "iPhone9,4", "D111AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.1.2", "iPhone9,4", "D111AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1.1 - iPhone 7 Plus
{ "12.1.1", "iPhone9,4", "D111AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.1.1", "iPhone9,4", "D111AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1 - iPhone 7 Plus
{ "12.1", "iPhone9,4", "D111AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.1", "iPhone9,4", "D111AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.0.1 - iPhone 7 Plus
{ "12.0.1", "iPhone9,4", "D111AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.0.1", "iPhone9,4", "D111AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.0 - iPhone 7 Plus
{ "12.0", "iPhone9,4", "D111AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.0", "iPhone9,4", "D111AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1.2 - iPhone 7
{ "12.1.2", "iPhone9,3", "D101AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.1.2", "iPhone9,3", "D101AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1 - iPhone 7
{ "12.1", "iPhone9,3", "D101AP", "_rootvnode", 0xfffffff00766a0c0},
{ "12.1", "iPhone9,3", "D101AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1.1 - iPhone 7
{ "12.1.1", "iPhone9,3", "D101AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.1.1", "iPhone9,3", "D101AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.0.1 - iPhone 7
{ "12.0.1", "iPhone9,3", "D101AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.0.1", "iPhone9,3", "D101AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.0 - iPhone 7
{ "12.0", "iPhone9,3", "D101AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.0", "iPhone9,3", "D101AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1.2 - iPhone 7 Plus
{ "12.1.2", "iPhone9,2", "D11AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.1.2", "iPhone9,2", "D11AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1.1 - iPhone 7 Plus
{ "12.1.1", "iPhone9,2", "D11AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.1.1", "iPhone9,2", "D11AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1 - iPhone 7 Plus
{ "12.1", "iPhone9,2", "D11AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.1", "iPhone9,2", "D11AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.0.1 - iPhone 7 Plus
{ "12.0.1", "iPhone9,2", "D11AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.0.1", "iPhone9,2", "D11AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.0 - iPhone 7 Plus
{ "12.0", "iPhone9,2", "D11AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.0", "iPhone9,2", "D11AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1.2 - iPhone 7
{ "12.1.2", "iPhone9,1", "D10AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.1.2", "iPhone9,1", "D10AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1.1 - iPhone 7
{ "12.1.1", "iPhone9,1", "D10AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.1.1", "iPhone9,1", "D10AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1 - iPhone 7
{ "12.1", "iPhone9,1", "D10AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.1", "iPhone9,1", "D10AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.0.1 - iPhone 7
{ "12.0.1", "iPhone9,1", "D10AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.0.1", "iPhone9,1", "D10AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.0 - iPhone 7
{ "12.0", "iPhone9,1", "D10AP", "_rootvnode", 0xfffffff0076420b8},
{ "12.0", "iPhone9,1", "D10AP", "_kernproc", 0xfffffff0076420d0},
//iOS 12.1.2 - iPhone SE
{ "12.1.2", "iPhone8,4", "N69AP", "_rootvnode", 0xfffffff0076020b8},
{ "12.1.2", "iPhone8,4", "N69AP", "_kernproc", 0xfffffff0076020d0},
{ "12.1.2", "iPhone8,4", "N69uAP", "_rootvnode", 0xfffffff0076020b8},
{ "12.1.2", "iPhone8,4", "N69uAP", "_kernproc", 0xfffffff0076020d0},
//iOS 12.1.1 - iPhone SE
{ "12.1.1", "iPhone8,4", "N69AP", "_rootvnode", 0xfffffff0076020b8},
{ "12.1.1", "iPhone8,4", "N69AP", "_kernproc", 0xfffffff0076020d0},
{ "12.1.1", "iPhone8,4", "N69uAP", "_rootvnode", 0xfffffff0076020b8},
{ "12.1.1", "iPhone8,4", "N69uAP", "_kernproc", 0xfffffff0076020d0},
//iOS 12.1 - iPhone SE
{ "12.1", "iPhone8,4", "N69AP", "_rootvnode", 0xfffffff0076020b8},
{ "12.1", "iPhone8,4", "N69AP", "_kernproc", 0xfffffff0076020d0},
{ "12.1", "iPhone8,4", "N69uAP", "_rootvnode", 0xfffffff0076020b8},
{ "12.1", "iPhone8,4", "N69uAP", "_kernproc", 0xfffffff0076020d0},
//iOS 12.0.1 - iPhone SE
{ "12.0.1", "iPhone8,4", "N69AP", "_rootvnode", 0xfffffff0076020b8},
{ "12.0.1", "iPhone8,4", "N69AP", "_kernproc", 0xfffffff0076020d0},
{ "12.0.1", "iPhone8,4", "N69uAP", "_rootvnode", 0xfffffff0076020b8},
{ "12.0.1", "iPhone8,4", "N69uAP", "_kernproc", 0xfffffff0076020d0},
//iOS 12.0 - iPhone SE
{ "12.0", "iPhone8,4", "N69AP", "_rootvnode", 0xfffffff0076020b8},
{ "12.0", "iPhone8,4", "N69AP", "_kernproc", 0xfffffff0076020d0},
{ "12.0", "iPhone8,4", "N69uAP", "_rootvnode", 0xfffffff0076020b8},
{ "12.0", "iPhone8,4", "N69uAP", "_kernproc", 0xfffffff0076020d0},
如果需要支持自己手中的设备,要么直接联系作者添加支持,要么就使用jtool2获取到自己设备对应内核的_kernproc函数地址,然后代码中调用void setKernelSymbol (char *Symbol, uint64_t Address);来设定符号_kernproc。
三、其他疑问
1. 直接用/Developer/usr/bin/debugserver拷贝到设备就可以调试,何必自己修改权限并且重签?
我的理解是,直接拷贝或者直接用xcode进行附加调试应用只能调试用户层的app,系统层的app没办法调试,比如SpringBoard,如果想调试系统级应用,就不能偷懒。
![]()
![]()